

In this page you find:
This section describes the Endian Switchboard and the functionalities it provides, including management options for the devices, the users, and their access rights.
New in version 5.0.5: The Endian Management Center.
The Endian Switchboard is a VPN-based solution that allows to control and manage complex infrastructures by providing a seamless connection of diverse remote devices, called endpoints, to a centralised server through gateways. Remote gateways and endpoints can be centrally managed directly from the switchboard or using the Endian ConnectApp, a desktop application that provides the same functionalities of the Switchboard. Devices can be accessed and managed by users, that are also created and managed on the switchboard, and can have different access levels to the gateways and endpoints. Endpoints can be accessed from remote workstations using application profiles.
Gateways can be added to the Switchboard literally in minutes by taking advantage of the Plug & Connect / Autoregistration procedure, that will take care of registering the gateway to Endian Network and of configuring the Green Zone and the VPN tunnel to the Switchboard. After the Plug & Connect procedure has been successfully completed, the gateway will be immediately available to the Switchboard users.
See also
A detailed description of the Plug & Connect procedure can be found in article Endian Cloud - Plug & Connect in the knowledge base.
More in detail, here follows the description of the various actors involved in the architecture.
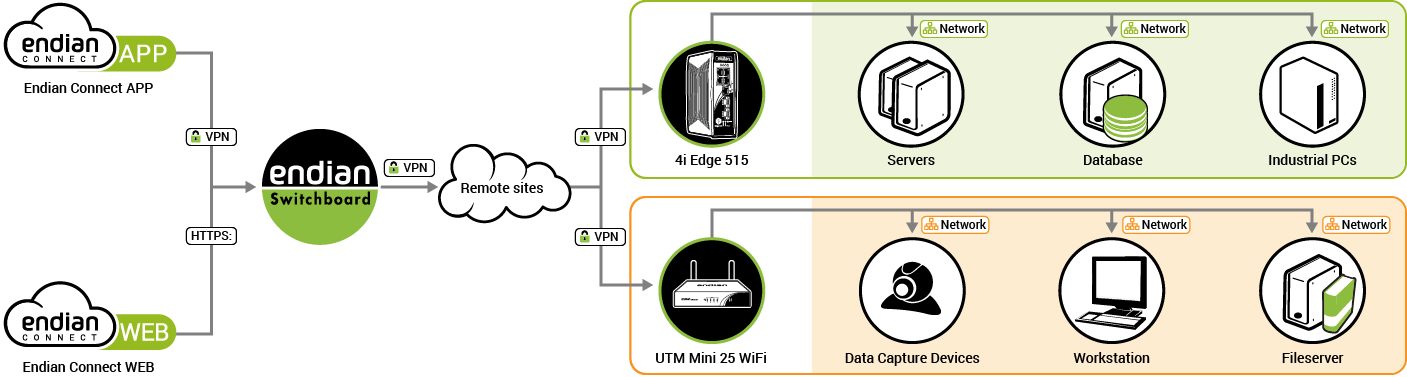
An example switchboard installation with most of the possible involved actors shown.¶
The Switchboard is the heart of the whole infrastructure. It stores all the configuration data about gateways and users, the log files, the access policies, and keeps track of the connections. It can be accessed in two ways:
By using a browser that points to the URL https://GREENIP:10443/manage/access, in which GREENIP is the IP Address of the appliance it is installed on.
By installing the ConnectApp on a workstation that accesses remotely to the appliance on which the Switchboard is installed.
An endpoint can be in principle any kind of equipment that can connect via Internet, so they can be any kind of industrial machinery, as well as remote workstation, servers and so on. Each endpoint has its own IP address and may connect to the local network and/or to the Internet by means other than the gateway. The only requirement is that the endpoint be reachable by the gateway.
Each endpoint can be connected to only one gateway and receives an unique IP address (called virtual IP in the architecture) that falls within the GREEN network of the gateway. The endpoint’s virtual IP may change when the size of the network needs to be accommodated, for example with the addition of new endpoints to the network.
A gateway is the door through which the Switchboard can manage and allow connections to endpoints. It can be easily configured and activated using gateway provisioning. Gateways are directly connected to the Switchboard by means of a VPN tunnel and takes care of routing connections between the Switchboard and the endpoints.
Gateways can be organised in groups and are usually in “normal” modality: they connect to the endpoints they control using their GREEN interface, and to the Internet using the RED interface. In some specific setups, gateways can be setup with an unique zone for both the uplink and the network. The GREEN subnet can be accommodated in size when the number of endpoints grows.
With device it is intended either an endpoint or a gateway.
A user is anyone who can in some way access and interact with either the Switchboard, a gateway, or an endpoint. Users can be arranged in user groups, in which a user can play two roles, either be a member or an administrator of the group. In the latter case, he can manage the members of the group.
An application is one method to remotely access to an endpoint from a remote workstation and is defined by a path on the workstation to the program executable and by optional command argument. Since there are several possibilities to connect to an endpoint, application can be grouped together in application profiles, that encompass all possibilities to access the same type of endpoint. Each endpoint has one application profile attached, that defines all the possibilities to reach it.
The basic access policy on the Switchboard is that a user can have access to one or more gateways and to all the endpoints managed by these gateways.
More advanced permissions can be granted to a user, including the ability to manage users, devices, applications, organizations and use the API.
The Endian Switchboard implements an additional access policy called Exclusive access, that can be granted at endpoint, gateway, or organization level. When this policy is enabled, only one user at a time can connect to that component, no one else can connect to it: When another user tries to access it, the switchboard prevents the connection. The rationale behind this policy is that when a user operates on a critical part of the infrastructure, like for example a gateway controlling several sensible endpoints, nobody else can interfere.
This policy is set globally: In the same Switchboard installation, there cannot be some organizations (resp. gateways, endpoints) that allow exclusive access and some that do not. Moreover, the policy is propagated downwards the hierarchy: If an organization is set to exclusive access, all the gateway have also the exclusive access set and the endpoints as well.
Finally, note that this policy can be disabled, granting concurrent access to all the infrastructure to everyone.
When deployed in large and complex scenarios, the management of users and devices on the Switchboard can be simplified by dividing all the available resources into small, self-contained units called organizations. Organizations can be organised in hierarchies and each of them consists of users, devices, and application profiles. The root organization retains some peculiar setting, called root node characteristics, see Organizations for details, while as a general rule, sub-organization inherit access policies and application profiles, although these can be overridden.
Note
If Organizations are not enabled on the Switchboard, various options concerning them are not present in the graphic interface.
Any instance of the switchboard can be accessed with different secure methods:
By accessing via HTTPS the public IP address or hostname of the Switchboards portal or to a UTM appliance with Switchboard module installed. This method works from any device, even from tablet and mobile phones, since the only requirements are a browser and an Internet connection.
By downloading the ConnectApp, Endian’s dedicated VPN client, from Endian Network (under Downloads ‣ Endian OpenVPN Client) and configuring an OpenVPN connection to the Switchboard. This method works only for Windows and Mac OS X desktop platforms but as a bonus allows to use third-party applications to connect to devices located behind the Switchboard.
Depending on the connection, the Dashboard page changes slightly. The next two screenshots highlight the differences: The connection to connect.endian.com or using the ConnectApp shows more information on the right-hand side: The number of online and total users, of online and total gateways, the total number of endpoints, and a few system information, namely the maximum number of users and gateways.
Moreover, the position of the menu-items like Dashboard, Users, and so on, are either on the left-hand side or on top of the window.
This page shows a number of information about the endpoints and gateways that are managed by the Switchboard and is divided into two tabs: Connections and Map. The former contains information about the connections to the devices, while the latter shows them on a world map, provided their location has been configured. Moreover, if the Message of the day under Settings ‣ Portal has been configured, it will appear on top of the page.
This page contains a table showing all devices configured on the Switchboard, along with the following information for each of them:
The device name, which may contain two different types of objects:
Gateways  and endpoints
and endpoints  , with the latter
indented to highlight their roles and the gateway they are connected
to. The icon of a device turns grey if they are offline, and green if
someone is connected to it.
, with the latter
indented to highlight their roles and the gateway they are connected
to. The icon of a device turns grey if they are offline, and green if
someone is connected to it.
Note
A small triangle on the left of a gateway denotes the presence of at least one endpoint managed by that gateway.
The groups to which the device belongs.
The organization to which the device belongs to.
A description of the device.
The device’s status, which is indicated with a string and one of the following icons:
 Online: The device is online and accepts connections.
Online: The device is online and accepts connections.
 Offline: The device is not connected to the Switchboard
Offline: The device is not connected to the Switchboard
 Connected: There is a connection to the device from the
local workstation.
Connected: There is a connection to the device from the
local workstation.
 In use: There is someone connected to the device, but a
nother concurrent connection is possible.
In use: There is someone connected to the device, but a
nother concurrent connection is possible.
 Busy: Someone is connected to the device, which cannot be
reached until he disconnects, because exclusive access has been
activated on that device.
Busy: Someone is connected to the device, which cannot be
reached until he disconnects, because exclusive access has been
activated on that device.
Above the table, different widgets are shown.
On the left-hand side, a set of buttons will allow to populate the table with only the devices that are in a given state; it is possible to show All devices, or only those that are in state Online, Offline, Connected, In-use, or Busy, simply by clicking on the button. These states are explained by the icons right above this paragraph.
In the middle, there is a switch that can be clicked to hide or show all endpoints at once, while on the right-hand side appears a filter, useful to search among all devices that are managed by the Switchboard. The matching devices will appear as soon as one character is written, concealing all those that do not correspond. The search takes place within all the fields in the table, making the filtering more effective.
When clicking on a device, either a gateway or an endpoint, an overlay appears, showing various types of information about the device.
In its upper part there are the names of the device and the organization it belongs to (if organisations have been enabled on the Switchboard), along with its status (online or offline).
The middle section contains two tabs, Applications and Logs. In the first one, Applications, there is the list of applications that can be used to connect to the device. The legend informs about the device status:
Active. There is an ongoing connection to the switchboard from the current workstation.
Busy. Someone is connecting to the device from another location.
Inactive. There is no connection to the device.
The Log Tab contains all the actions and events that took place on the selected device. The log shown here are the same that can be found in the Switchboard’s Logs section, when applying a filter containing the name of the device. More information about the data contained in the table and the actions logged can be found in the above-mentioned Logs section.
At the bottom, the information displayed depends on the device: in case of a gateway, its name and the name of organization it belongs to are shown, whereas in case of an endpoint, also its real and virtual IP address and the gateway through which it is reachable are shown.
Note
To remotely connect to an endpoint, an application uses in most cases the virtual IP Address assigned by the Switchboard, although in some cases the real IP address is required.
The Switchboard Map is a useful feature that shows all of the configured gateways and endpoints on a world map, based on OpenStreetMap and leaflet. In order to show the appliances on the map, they must be configured appropriately with a valid address.
The location can be set individually for each device under
Menubar ‣ Switchboard ‣ Devices, after clicking
on the pencil icon  next to the device, then on the
Location tab. See Location for details.
next to the device, then on the
Location tab. See Location for details.
When the Map tab is opened and there are devices which have not yet defined their location, an overlay box ask whether to define it now or later . A click on Set later dismisses the overlay and opens the map, while a click on Set location will open a list of devices for which the location is missing.
Here, for each device, write a city and possibly an address in the
given textfield, then click on the ![]() icon on the right-hand
side to confirm the location. A quick search will show the correct
name as retrieved from OpenStreetMap and the device will be
immediately placed on the map and shown. A click on the
icon on the right-hand
side to confirm the location. A quick search will show the correct
name as retrieved from OpenStreetMap and the device will be
immediately placed on the map and shown. A click on the  check mark that replaced the search icon will show the just placed
gateway on the map. If the address is not found the search icon is
replaced with
check mark that replaced the search icon will show the just placed
gateway on the map. If the address is not found the search icon is
replaced with  .
.
To exit the overlay, simply click on the X on the upper right corner and you will see on the map all the devices for which the location has been set.
When opened, the world map shows all the devices whose location is known, each identified with its name and an icon, that can be clicked to show some information. Around the map, many widgets allow to carry out different actions on the map.
On the top right corner, a search bar allows to quickly find a given device. After a few characters are written, a list of possible matches is shown, from which to choose the desired one, gut if there is only one result, it will be immediately shown on the map.
On the left-hand side, a few icons allow to carry out some actions on the map:
 Zoom in the map.
Zoom in the map.
 Zoom out the map.
Zoom out the map.
 Open the map in full screen mode.
Open the map in full screen mode.
 Open the map in a new tab.
Open the map in a new tab.
 Open the list of the devices’ locations, to check or modify
them.
Open the list of the devices’ locations, to check or modify
them.
Hint
It is possible to zoom the map also using the mouse wheel.
On the bottom right corner, a buttons is shown, depending if the map is in search or normal mode.
Exit from the current search and go back to the full map.
Reset the current filters.
Hint
As a shortcut for the buttons, press the ESC key.
This page is composed of two tabs, namely Users and Groups. In the former, user management can be carried out, while in the latter, users can be arranged into groups.
In this page, all the users having the rights to connect to the Switchboard are listed in a table that shows the following data:
The e-mail of the user, which acts also as username.
A description of the user (e.g., the real name).
The groups the user belongs to.
The actions that can be carried out on each user:

 - enable or disable the user.
- enable or disable the user.
 - modify the user.
- modify the user.
 - remove the user.
- remove the user.
 - see user’s activity log.
- see user’s activity log.
New users can be added by clicking on the Add User link at the top of the page, while the certificate needed by the users to connect to the Switchboard can be downloaded by clicking on the Download CA Certificate link.
In the users editor, the configuration options that can be defined are grouped into these tabs: User, Groups, Permissions, Additional user information, and Provisioning.
This tab gives access to some basic information about the user.
The username for the new user. It must be unique.
The organization to which the user belongs to. This option is available only if at least one organization has been created.
The real name or a description of the user.
Tick the checkbox to rely on a remote server for authentication. If selected, the two next options disappear.
Note
The remote server must be configured under Menubar ‣ VPN ‣ Authentication ‣ Settings.
The new password for the user, to be inserted twice for confirmation. On the right-hand side of each field, a checkbox can be ticked to display the password.
This field shows a string that can be used as token for the 2-factor authentication by the users of the switchboard. There are two buttons underneath:
Create a new authentication string.
By clicking on this button, a QR code is shown on the monitor, that can be acquired by the user’s smartphone and used when authenticating to the Switchboard. The button is active only when a secret has been generated.
Note
These options are only displayed if an authentication server of type One Time Password has been defined under Menubar ‣ VPN ‣ Authentication ‣ Settings and it has been mapped to the Switchboard service in the Authentication server mappings.
In this tab there is a Multiselect box that allows to choose the groups that the user is member of. At least one user group must have been defined.
The role that the user can assume in every group: either member of or administrator of. One role per selected group can be chosen.
In this tab can be selected the permissions a user has on the other nodes and users of the Switchboard. Items on the right column of the multiselect box are the permissions granted to the user, while those in the left column can not be used by the user. Click on the + on the right-hand side of the item to grant a permission, on - to remove the permission.
The user can be granted several permissions:
Superuser (full control): The user can fully manage the Switchboard.
Access to sub organizations: The user can access other organizations down the hierarchy.
Manage profile The user can edit and modify profiles.
Manage users The user can manage other users.
Manage devices The user can edit and modify devices.
Manage applications: The user can manage the applications.
Manage organizations: The user can manage the organizations.
Use the API: The user can access and use the Switchboard’s API.
Push route to GREEN | BLUE | ORANGE zone: When one or more of these options is selected, appropriate routes to the subnets governed by the Switchboard will be pushed to the user.
Any combination of these values can be associated to the user.
Hint
It is possible to use the two shortcuts Add all and Remove all to assign or remove all permissions at once.
More detailed information about the user can be supplied in this tab, including the certificate to be used for the authentication.
The address of the user, split into two lines if necessary.
The city where the user is located.
The city’s ZIP code.
The state or the province where the user is located.
The country where the user is located, chosen from the drop-down menu.
The user’s job or role.
The company that employs the user.
The drop-down menu allows to configure the user’s certificate. The available options are:
Don’t change. Leave the current certificate. If the user has yet no certificate, one must be created.
Generate a new certificate. Create a certificate.
Upload a certificate . Upload a user certificate.
Upload a certificate request. Upload a user certificate request.
If no certificate has been assigned to the user, the message Create a certificate via the ‘Certificate configuration’ is shown.
Additional options appear when selecting an option, except for the Don’t change choice.
By choosing Generate a new certificate, these new options are:
The alternative name for the subject, which allows a single certificate to be associated to multiple domains or resources. The available options are:
DNS. The DNS entry of the site
IP. The IP address of the site
email. An email address.
The actual value for each option must be written in the textbox on the right.
The name of the organisation unit to which the user belongs to.
The name of the users’ organisation.
How many days the certificate is valid.
A password to protect the file in which the certificate is stored.
The algorithm used to encrypt the certificate, chosen among the available options: SHA1, SHA2 224, SHA2 256, SHA2 384, or SHA2 512.
When selecting Upload a certificate, these options show up:
By clicking on the Browse button or on the textfield, a file chooser will open, in which to supply the path to the certificate to be uploaded.
The password for the certificate, if needed.
Finally, the following two options appear with the choice of Upload a certificate request.
By clicking on the Browse button or on the textfield, a file chooser will open, in which to supply the path to the CSR to be uploaded.
How many days shall the certificate be valid.
In this tab appear two options for the management of the Endian Network credentials for the user.
The username used to access Endian Network.
The password of the Endian Network account or the Endian UTM Appliance’s registration key.
Hint
Click on the checkbox on the right-hand side of the option to show the password.
A user group is a set of users that have access to one or more gateways or gateway groups with specific roles and permissions.
The page initially shows only the Add new User Group link and an empty table, that will carry the list of all the groups and some information about them:
The name assigned to the group.
A description of the group.
The available actions on each of them:
 - Modify the user group.
- Modify the user group.
 - Remove the user group.
- Remove the user group.
 - View the log files for the user group
- View the log files for the user group
When clicking on the Add new User Group link (that becomes Add Group when at least one group already exists), the Editor opens right above the table. In the three tabs that compose the editor, new user groups can be defined.
This is the tab in which to define a new user group.
The name given to the group. It is mandatory and must be unique.
The organization to which the group belongs to. This option is available only if at least one organization has been created.
A description of the group.
In this tab it is possible to add users to group, using a Multiselect box.
Select which users belong to the group and their role: From the multiselect box Add as choose the role, which is either member of or administrator of the group, then the user(s), by clicking on the + next to each user.
This page contains two tabs, Devices, in which to manage all devices reachable from the switchboard, and Groups, in which to configure groups of devices.
This page contains a table with the list of all the gateways that have already been configured. Above the table, three links are shown: Plug & Connect (Autoregistration), Add gateway, and Download CA certificate, which are described further on.
The table displays for every device the following information:
Its name.
The organization it belongs to.
A description.
The serial number.
The groups of which the device is part.
The available actions:

 - enable or disable the gateway.
- enable or disable the gateway.
 - modify the gateway.
- modify the gateway.
 - copy the gateway.
- copy the gateway.
 - remove the gateway.
- remove the gateway.
 - see gateway’s activity log.
- see gateway’s activity log.
 - Download the gateway configuration.
- Download the gateway configuration.
Note
The configuration of a gateway is a text file that contains all the configuration options and the certificate used by the gateway.
The first link, Plug & Connect (Autoregistration), allows to start the registration of a remote gateway to the Switchboard. This three-steps procedure needs a remote device connected to the Internet and a valid Activation Code for that device. By clicking on the link, a new panel appears, in which only one option is available.
Supply the activation code for the remote device to be connected.
After clicking on the Next >> button, a new screen appears, showing an image of the Appliance and with a few options.
A description for the appliance. The default, self-generated value can be accepted.
Enter the password for the admin user, who will access the appliance by HTTPS.
Enter the password for the root user, who will access the appliance by SSH or by console.
In order to use the same password for both users, tick this checkbox.
After this step, it is necessary to connect the WAN port of the remote appliance to the Internet, for the last step of the procedure.
Hint
The remote device must be able to communicate using port 443 TCP for the procedure to complete successfully.
After a few minutes the new gateway will be shown in the list along the already registered gateways on the Switchboard. If for some reasons the procedure is not successful, error messages are shown, along with the link to the troubleshooting document.
See also
A detailed description of the plug & connect procedure, which includes the requirements to start the procedure, a more in-depth description, and troubleshooting options, can be found in article Endian Cloud - Plug & Connect.
When clicking the Add gateway link, the gateway editor will open right above the table and a new device can be created. The editor consists of several tabbed pages, in which to configure all the different options of the gateway.
When clicking on the Download CA certificate link, the Switchboard’s CA certificate will be downloaded. This certificate must be used when configuring the VPN connection on the device itself.
This tab contains the basic setup options for the gateway.
The name assigned to the new gateway, which must be unique. A default name is generated, but can be changed at will.
The organization to which the gateway belongs to. This option is available only if at least one organization has been created.
A description for the device.
The serial number of the gateway. This option is displayed only if Auto registration is not enabled.
Tick the checkbox to rely on a remote server for the passwords used by the gateway. If selected, the two next options disappear.
Note
The external provider must be configured under Menubar ‣ VPN ‣ Authentication ‣ Settings.
The password to access the gateway. Tick the checkbox on the right-hand side of the textbox to show in clear text the password. This option is displayed only when Auto registration is disabled.
Tick the checkbox to enable the device.
In this tab it is possible to choose from a multiselect box to which groups the gateway will belong, provided some groups have already been defined in the Switchboard ‣ Devices ‣ Groups page, see Groups of devices.
This tab contains information about all the endpoints that can be reached from the gateway and can be used to manage them.
The first information to be supplied is an approximate estimate of the endpoint that will be governed by the gateway.
Note
This information is particularly relevant, as it is used to create a virtual network in which to accommodate all the IPs assigned to each endpoint. In case of doubt, choose a size larger than the actual number of endpoints, otherwise the network might not suffice to accommodate additional endpoints.
The network used by the endpoints, in CIDR Notation.
When this checkbox is ticked, the endpoint will not be accessed via its virtual IP address, but via its real IP address.
Note
If selected, the next option is not available.
The virtual IP address to be assigned to the endpoint.
Note
When the option Enable automated virtual subnet assignment in the switchboard network settings section is enabled, this option does not appear. Indeed, an IP address for each endpoint is automatically assigned by means of the above mentioned option.
A table showing all the endpoints controlled by the gateway, along with those information:
The name of the endpoint.
The endpoint’s IP address.
A description of the endpoint.
The application profile used to access the endpoint.
The Enabled status, i.e., whether the endpoint is active or not.
The Source Nat status. If active (“yes”), the endpoint will see all the traffic as originating from the gateway. This set up can prove useful when e.g., the Endpoint is situated behind a firewall and can not communicate with the outside.
A custom field.
Each field in each table’s row can be edited by double-clicking on it: Depending on the type of information it carries, each field can show a drop-down menu (i.e., a “yes-no” choice for the Enabled column, or the available profiles for the Application Profile) or a text field (all the other).
The management of the endpoints can be done using the buttons at the bottom of the table:
This option allows a new endpoint to be added to the gateway. Its configuration can be carried out by double-clicking on the fields of the new row.
By clicking on this button, the highlighted endpoint is removed from the gateway. This button is active only when one row is selected.
Warning
The deletion of a row is immediate and can not be reversed.
This button toggles the table with a textfield, containing the same information present in the table in CSV format, useful to export the configuration of all endpoints.
The users or groups of users that shall have access to this gateway can be added from the multiselect box in this tab. Each user can assume the role of either regular user or manager of the gateway.
If a group is selected, all members of that group can be selected as regular user or manager.
In this section it is possible to define the configuration for a remote gateway. The available configurations options are:
Choose the model of the device from those available in the drop-down menu.
The activation code used to set up the gateway.
Immediately after the choice of the model, all the configuration options for it will be displayed and can be configured.
Note
Depending on the type of the model chosen, some of the options available will be filled in with suitable values.
Choose the password for the root user, used for SSH (console) access.
Choose the password for the admin user, used for HTTPS (browser) access.
The hostname of the gateway
The gateway’s domain name.
The company to which the gateway belongs
The reference e-mail for the gateway, usually of the responsible person for that gateway.
The timezone in which the gateway is located.
The country where the gateway is located.
The type of the RED interface, i.e., how the gateway connects to the Internet. Four types are available: DHCP, Static, No uplink, and 3G.
The interface that connects the gateway to the Internet. The available options in this drop-down menu are determined by the Model chosen above. This option does not appear when the Red type is set as No uplink
The following options are displayed according to the selected type of red device. By choosing DHCP, none of them will appear.
The IP address of the RED interface. This option appears only when the RED type is Static.
The IP address of the gateway for the RED interface. This option and the next one is needed to access the Internet and appears only when the RED type is Static or No uplink.
The IP addresses of the DNS server used by the gateway, one per line. It appears only when the RED type is Static or No uplink.
The name of the access point, appears only in the 3G/4G and UMTS Red Type.
This option appears only for the 3G/4G Red Type and allows to select the type of modem to be used from the drop-down menu, among those available: 3G/4G or CDMA
The interface of the GREEN zone, i.e., the one in which the endpoints are situated.
The IP address pool assigned to the GREEN zone.
The interface of the BLUE zone.
The IP address pool assigned to the BLUE zone.
The interface of the ORANGE zone.
The IP address pool assigned to the ORANGE zone.
A custom address used by the endpoint to connect to the OpenVPN server.
Hint
The format to be used for the address in this and in the next option is hostname.domain:port:protocol or IP.address:port:protocol, with the port or protocol as optional, hence valid values include vpn.example.com:1197:udp and 123.45.67.89:1192.
If the protocol is specified, the port must be specified as well.
A custom address used by the endpoint to connect to the fallback OpenVPN server.
Tick the checkbox when the gateway uses a proxy for its connection to the Internet. The next four options will appear to configure that proxy.
The IP address of the upstream proxy server.
The port on which the proxy service runs on the server.
The username to connect to the proxy server, if needed.
The password to connect to the proxy server, if needed.
Click the checkbox if the upstream HTTP proxy requires NTLM Authentication.
If the upstream HTTP proxy needs to be contacted with a given user-agent, write it here.
The options in this tab can be used to define on the gateway suitable port-forwarding rules that allow to redirect traffic coming from an endpoint to a given host. The port forwarding rules are pushed on the Gateway via the OpenVPN connection.
The table contains the following information for each endpoint.
Endpoint. The endpoint for which the rule is defined. No choice is available if no endpoint has already been set up.
Incoming IP. The gateway’s public IP address on which to apply the rule.
Incoming ports/ranges. The port or range of ports on which to apply the rule.
Protocol. The protocol that shall be used in the rule: Available choices are tcp, udp, tcp+udp, or icmp.
Remote IP. The remote IP address to which the traffic is forwarded.
Remote port/range. The port on the remote IP to which the traffic is forwarded.
Description. A custom remark about the gateway.
Each field in each table’s row can be edited by double-clicking on it: Depending on the type of information it carries, each field can show a drop-down menu (i.e., the list of the endpoint for the Endpoint column, or the available protocols for the Protocol columns), or a text field (all the other).
The management of the rules associated with the endpoints can be done using the buttons at the bottom of the table:
This option allows to add a new rule. Its configuration can be carried out by double-clicking on the fields of the new row.
By clicking on this button, the highlighted rule is deleted from the set. This button is deactivated if no row is selected.
Warning
The deletion of a row is immediate and can not be reversed.
This button toggles the table with a textfield, containing the same information present in the table in CSV format: This proves useful to export the whole set of rules.
In this tab it is possible to assign a location to the device using either the Location Editor Map or the two small text fields below.
In the map, use the  and
and  buttons to resize the
maps to your needs or use directly the text field.
buttons to resize the
maps to your needs or use directly the text field.
In this textfield, write an address and optionally also the city and country. If a match is found, an icon is positioned on the map, if more result are available, choose the most appropriate one.
Note
When an address is selected, the two textfields below are automatically filled in.
It is also possible, instead of supplying the address, to give the coordinates of the device location:
Enter in decimal form the latitude where the device is installed
Enter in decimal form the longitude where the device is installed.
If the device is moved from its current location into a nearby one, it is possible to drag the icon to the new location: the new address and coordinates will be updated automatically.
The page contains only the Add group link above a table (initially empty) carrying the list of all the existent groups and some information about them:
The name assigned to the group.
A description of the group.
The available actions:
 - modify the gateway group.
- modify the gateway group.
 - remove the gateway group.
- remove the gateway group.
 - see gateway group’s activity log.
- see gateway group’s activity log.
When clicking on the Add group link, the editor opens right above the table. The setup options are grouped in three tabs: Group, Members, and Permissions.
This tab contains basic information about the group.
The name assigned to the group.
Note
This name must be unique within gateway groups and is the first option to be defined.
The organization to which the group belongs to. This option is available only if at least one organization has been created.
A description of the group.
This tab contains information about the members of the group. Two options are available:
The IP pool from which all devices in the group obtain an IP address.
Hint
Use CIDR notation for the pool.
Choose which gateway are part of this group.
Select all users that can access this group and the role (i.e., either regular user or manager) they can assume.
There are two tabs in this page: Applications, in which to define all possible means to connect to an endpoint, and Profiles, in which to group together several applications and assign them to a device.
An application can be seen as a means to access from a remote PC or workstation equipped with the Endian S.r.l., Italy ConnectApp to an endpoint or to a service running on an endpoint, possibly using a third-party software installed on the workstation.
The page initially shows the Add application link and a table containing the applications available by default and other information:
The name given to identify the application.
The type of the application (see further on for more information).
Some details about the protocol and port(s) used by the application.
A description of the application
The available actions for each application:

 - Enable or disable the application.
- Enable or disable the application.
 - Modify the application.
- Modify the application.
 - Remove the application.
- Remove the application.
Above the table, on the right-hand side appears a filter, useful to search among all applications that have been defined in the Switchboard.
When clicking on the Add application link, the applications editor opens right above the table, giving the opportunity to define additional applications.
Two tabs are present in this editor: Application and Advanced parameters. The latter appears only for some of the Application type available.
A name to identify the application.
The name of an organization to which the use of the appliance is reserved. At least an organization must have been defined in the Organizations section for this option to appear.
A description of the application.
The type of the application, which can be selected from the drop-down menu.
Note
The choice of the application type influences also the availability of some of the next options; also the options that appear in the Advanced parameters tab will depend on the application type chosen.
The protocol that the application should use, chosen from the drop-down menu. It can be TCP, UDP, or TCP & UDP.
The port used by the application.
The URL to be used for the connection. This option is available only when the Application type above is either HTTP or HTTPS.
Tick the checkbox to enable the application.
The next options appear only if the Application type above is Custom and allow to define the path on the workstation to launch the application and arguments to be passed to the program. Since a same application might be run on Microsoft Windows and Mac OS X, the path and the arguments can be specified twice, once for each OS. It is even possible to use placeholders, that will be replaced accordingly on the operating systems, see below for more details.
The full path to the program to use.
Additional arguments to be passed to the program.
The next options concern how the ConnectAPP launches the application to connect to the remote device. The options are available for Windows and Mac OS X.
By selecting this option, the ConnectAPP will use its integrated application for the remote connection.
By ticking this checkbox, it will be possible to specify which external application will be launched to establish the connection to the remote device. Two more option will appear, Command path and Command arguments, that are exactly the same described above and for which it is possible to use the placeholders described next.
Available palceholders.
The purpose of a placeholder is to allow the same application to be used on every device, independently of the varying configuration values of each device, like for example their (public) IP addresses.
Placeholders can be used in the HTTP, HTTPS, and Custom application types.
For HTTP and HTTPS types, these are the available placeholders:
%DEVICE_IP% the IP address assigned to the device.
%PHYSICAL_IP% the physical IP of the device.
%SERVER_EXTERNAL_HOST% the FQDN of the server’s public hostname.
%SERVER_INTERNAL_IP% for the internal, private IP address.
In the Custom application type, the available placeholders are:
%PROGRAM_PATH%: The default installation directory for applications (usually C:\Program Files).
%SYSTEM_DRIVE%: The drive containing the Windows root directory (C:\).
%SYSTEM_ROOT%: The Windows root directory (C:\Windows).
%HOME_PATH%: The user’s home directory (C:\Documents and Settings`username`).
As an example of application, suppose that each workstation equipped with Windows and the ConnectApp has also the program PuTTy installed in user’s home directory. To allow users to use putty to connect via SSH, define an application with the following configuration values:
Name: PuTTy -SSH
Description SSH via PuTTy
Application Type: Custom
Protocol: TCP
Port: 22
Command path: %HOME_PATH%\putty.exe
Command args: username@%DEVICE_IP%
Note that username must be a valid user account on the endpoint.
Depending on the application type chosen in the other tab, the following common options are available for all types except for Custom.
See also
To find more detailed information about the configuration of the advanced options of the VNC, RDP, SSH, and Telnet connections, refer also to the Connection configuration section in the guacamole manual.
The username used for the remote login.
The password that is used for the login, repeated twice for confirmation.
There is also the possibility to define advanced options for the following types:
SSH
Use the textfield to paste the private key used for the connection.
Write here the passphrase that corresponds to the private key.
Select from the drop-down menu the colors used in the SSH terminal.
The font used in the terminal.
The size of the font.
RDP
There are a number of options that can be configured with this type of connection, but they are not required in most cases. These options allow to customise the authentication, the session, the audio support, some performance boost, and the RemoteApp.
VNC
The number of times the connection should be attempted after an unsuccessful try.
Choose the color depth used for the connection.
Invert the red and blue colours.
Choose from the drop-down menu whether to use the local or remote cursor.
Tick the checkbox to disallow the client to make changes on the remote device.
The encoding to assume for the VNC clipboard. This should be changed only if the VNC server supports encodings different from the standard ISO 8859-1.
Telnet
The regular expression that recognises the correct moment when to send the username to the remote device.
The regular expression that recognises the moment when to send the password to the remote device.
Select from the drop-down menu the colors used in the SSH terminal.
The font used in the terminal.
The size of the font.
Custom
For custom applications, click on Add row to add a new parameter, and then fill in the following information:
The name of the parameter.
The value of that parameter.
It is possible to add any number of options and their values, these will be passed on the command line to the application.
Applications can be grouped together into Profiles and attached to single endpoints, tailoring the possibility to access them. In other words, it is possible to configure applications on a given endpoint so that it can be reached only via some given protocols (e.g., RDP, SSH or HTTP) or services (e.g., VNC). The choice of the applications can be influenced also by the endpoint’s running operating system and services.
The page contains the Add profile link, above the table carrying the list of all the available profiles and some information about each profile:
The name given to the profile.
The applications that are part of the profile.
The available actions on each of them:
 - Modify the application profile.
- Modify the application profile.
 - Remove the application profile.
- Remove the application profile.
Note
In case one or more profiles are deleted, the single applications will not be deleted: To remove an existing application, go to Applications.
Above the table, on the right-hand side appears a filter, useful to search among all profiles that have been defined in the Switchboard.
When clicking on the Add profile link, the editor opens right above the table. Here, additional profiles can be created, by supplying the following information:
A name to identify the profile.
Select for which organization the Profile will be available.
A note about the profile.
Available applications are listed in this multiselect box. To add an application to the profile, click on the + next to the application’s name. To search for an application, use the textbox on top of the box. The Add all link can be used as a shortcut for moving all applications within the profile. An application can be removed from the profile by clicking on the - next to the application’s name in the right column.
An important feature of the Switchboard are Organizations that have been introduced to add support for a more granular division of complex enterprises into smaller, self-contained units -called indeed organizations, which can be arranged into hierarchies.
Note
Organizations are not enabled by default on the Switchboard; they are a feature that must be requested when purchasing a Switchboard licence.
A Switchboard organization consists of one or more users and of one or more devices, be it gateways or endpoints. Users and devices within one organization can not see, access, or manage users and devices in other organizations. A user, a user group, or a device can belong to exactly one organization.
Within an organization, the default policy is that users can see all other users and all the devices in sub-organizations that are lower in the hierarchy.
The hierarchy within an organization consists of an unordered tree with a root node and at least one children or descendant, each node being one (sub-)organisation within the organization.
From a technical viewpoint, the sub-organisations are a bit different from the root node: Indeed the latter has some properties that the children inherit and cannot modify, because they are inherent to the whole organisation or to the Switchboard installation. These root node characteristics are:
OpenVPN: dedicated servers or instances, possibly with a fallback, and public IP address of FQDN.
A dedicated IP address pool, with manual or automatic virtual subnet assignment.
The possibility to push the entire virtual IP pool to the clients connected.
A unique Switchboard bind IP address, possibly with fallback.
This page initially contains an empty table of the available organizations, and some information about each of them:
The organization’s name.
The path (from the root organization)
The available actions on each organization:
 - Modify the organization.
- Modify the organization.
 - Remove the organization.
- Remove the organization.
A link above the table, Add Organization, allows to define a new organization.
In the editor, the options available to create a new organization are grouped into four tabs, namely Organization, Network, Portal, and Provisioning.
An identifier used for the identification of the organization, which must be unique within the instance of the Switchboard. This identifier is mandatory for the new organization.
If this is not the root organization, select from the drop down menu its parent.
Select from the drop-down menu whether to enable or disable exclusive access to the whole organization.
Define the highest number of nodes that will be allowed within the organization.
The name of the organization.
The VAT number of the organization.
The address of the organization.
The city in which the organization is located.
The city’s ZIP code.
The state or province in which the organization is located.
The country in which the organization is located.
The e-mail of the organization.
The website of the organization.
The phone number of the organization.
The Fax number of the organization.
Tick the checkbox to enable the remote API.
A string used as the key for accessing and using the API.
It is the IP address on which the Switchboard listens for connections. It is mandatory when more IP addresses are assigned to the Switchboard.
This option only appears if on the Endian UTM Appliance multiple instances of the OpenVPN server are running. Choose the instance to be used for the Switchboard from the drop-down menu.
The public IP address or FQDN to be assigned to the Switchboard.
Tick the checkbox to allow a fall back instance of the OpenVPN server, in case the main one can not be reached. The next two options will appear.
The fallback OpenVPN instance used in case the one specified in the previous option does not run, chosen from the drop-down menu.
The public IP address or FQDN to be assigned to the fallback server of the Switchboard.
Tick this checkbox to allow the virtual IP addresses for the subnets to be automatically assigned. When enabled, the next option appears.
This options defines the IP address subnet for the addresses of the gateways.
With this option enabled, whenever a client connects, the whole virtual IP subnet will be pushed to it.
Write in the textfield the FQDN to which users can connect to access the Organization’s portal.
The message displayed to the users that connect to the portal.
Tick this checkbox to enable the receipt on notification messages.
When this checkbox is ticked, gateway provisioning is enabled. See below for more information.
The username for accessing Endian Network, used for the automatic registration of the gateways.
The registration key of the endpoint. Tick the checkbox on the right-hand side to show the password, which is otherwise hidden.
Choose from the drop-down which should be the default model of new-added gateways.
New in version 5.0.5.
This page is divided into three tabs, presenting statistics about the Organizations, the Users, and the Devices respectively, that exist on the Switchboard. Each tab contains a table, with a filter bar above it, that allow to search within the elements in the table:
Filter: a research string.
Organization: select from the drop-down menu the Organization in which to search.
From, To: select the time interval in which to look up. To select a given day, select it in both the From and To fields.
This page shows a table containing the list of currently defined organizations, with a number of information. This tab does not appear if Organizations are not enabled on the Switchboard.
Note
The numbers in parenthesis are the values of the child organizations.
Organization. The name of the organization, along with its ID and its path from the root organization.
Users. The number of users that belong to the organization.
Devices. The number of devices, which are grouped in three categories: Gateways, Endpoints, and Endian Appliances.
Nodes. Two values associated with the nodes: Counted nodes - the number of nodes the organization has, and Node limit - The maximum number of nodes allowed.
Traffic. The amount of traffic Sent from or Received by the organization.
This page shows a table containing the list of the users that have connected through the Switchboard.
User. The account name and the organization it belongs to.
Organization. The name of the organization, along with its ID and its path from the root organization.
Note
This column appears only if Organizations are enabled on the Switchboard.
Connections. To Switchboard is the number of connections to the switchboard made by the user, while To devices the number of connections to devices.
Connections Time. To Switchboard is the amount of time spent by the user on the switchboard, while To devices the time spent on the devices.
Traffic. The amount of traffic that has been made by the user, divided into Sent by the user and Received from the user.
This page shows a table containing the list of devices connected to the Switchboard and a number of information about them.
Device. The name of the device and the organization it belongs to.
Organization. The name of the organization, along with its ID and its path from the root organization.
Note
This column appears only if Organizations are enabled on the Switchboard.
Connections. To Switchboard is the number of connections to the switchboard made by the device, By users shows how many users have connected to the device.
Connections Time. To Switchboard is the amount of time during which the device has been connected to the switchboard, while By users is the amount of time during which the users were connected to the device.
Traffic. The amount of traffic that has been made by device, divided into Sent by the device and Received from the device.
Changed in version 5.0.5: This setting page has been completely redesigned.
This page allows to set up all the global configuration options of the Switchboard. Before actually configuring the Switchboard, it is mandatory to accomplish two tasks in two other modules: Firewall and VPN.
The first task consists in the activation of the VPN Firewall, as this
is required by one option in the OpenVPN server. To complete the task,
go to Menubar ‣ Firewall ‣ VPN Traffic and, if
not yet active, click on the grey switch  .
.
Once that the VPN firewall has been enabled, the second task requires to set up a couple of options in the VPN module.
Indeed, the Switchboard relies on an OpenVPN instance running on the Endian UTM Appliance to provide secure connections between the clients and the devices. While most of the OpenVPN instance’s parameters can be freely chosen, two of them must be configured as follows:
The traffic on the OpenVPN’s device must be routed.
The traffic between the clients must be filtered.
The configuration options interested are:
In the Network options, the Bridged checkbox must not be ticked. Hence, if TAP is selected, do not tick the checkbox.
Note
When the TUN device is chosen, the traffic can only be routed and the checkbox is not accessible.
Under Advanced Options, the option Client to client connection should be set to Filter connection in the VPN firewall.
More information about the aforementioned options can be found under Menubar ‣ VPN ‣ OpenVPN server ‣ Server configuration.
This page contains four tabs, which group all configuration options for the Switchboard: Settings, Network, Portal, and Provisioning.
This option sets the FQDN through which the Switchboard is reachable.
Choose from the drop-down menu which certificate shall be used for this Switchboard instance
Hint
A new certificate can be created under VPN ‣ Certificates.
Tick the Cehckbox to enable the Management center. See Section Management Center for details.
This options governs the ability to lock single endpoints within a gateway, or even a whole gateway, allowing exclusive access to one user at a time. Three options are available, disabled -no exclusive access is granted, on gateway level -a whole gateway including its endpoints can be locked, and on endpoint level -single endpoints can be locked.
When the checkbox is ticked, an ICMP ping packet will be periodically sent through the VPN tunnel to ensure the connection is still alive.
When enabled, the next two options appear.
The interval between two successive checks.
How many times a failed check will be re-issued before the VPN connection is considered dead.
Tick the checkbox to enable the remote API.
A string used as the key for accessing and using the API.
It is the IP address on which the Switchboard listens for connections. It is mandatory when more IP addresses are assigned to the Switchboard.
This option only appears if on the Endian UTM Appliance multiple instances of the OpenVPN server are running. Choose the instance to be used for the Switchboard from the drop-down menu.
The public IP address or FQDN to be assigned to the Switchboard.
Tick the checkbox to allow a fall back instance of the OpenVPN server, in case the main one can not be reached. The next two options will appear.
The fallback OpenVPN instance used in case the one specified in the previous option does not run, chosen from the drop-down menu.
The public IP address or FQDN to be assigned to the fallback server of the Switchboard.
Tick this checkbox to allow the virtual IP addresses for the subnets to be automatically assigned. When enabled, the next option appears.
By ticking this checkbox it becomes possible to choose IP addresses subnets for each gateway group.
This options defines the IP address subnet for the addresses of the gateways.
With this option enabled, whenever a client connects, the whole virtual IP subnet will be pushed to it.
This page allows to configure the portal and contains initially only two options.
Tick the checkbox to reveal a new panel showing more configuration options.
The message displayed to the users that connect to the portal.
Tick this checkbox to enable the receipt on notification messages.
A message shown to all users connecting to the Switchboard.
In this tab it is possible to specify the options for the gateway provisioning. Initially it contains only an option and a list of models.
Tick the checkbox to enable provisioning. The next options will appear.
Tick the checkbox to send the configuration of the provisioning to Endian’s repository of configuration. Endpoints will be able to download these configurations file and self-configure themselves.
New in version 5.0.5.
The username used to access Endian Network
The password of the Endian Network account or the Endian UTM Appliance’s registration key.
Copy and paste here the content of the .pem certificate file selected for the provisioning.
Copy and paste here the content of the .pem file containing the private key corresponding to the selected certificate..
Choose from the drop-down which should be the default model of new-added gateways.
New in version 5.0.5.
At the bottom of the page, it is possible to add new models of Endian appliances that can be used in the provisioning.
The table consists of those fields:
The name given to the gateway.
The name of the network interfaces available in the appliance. The Default models panel below the table can be used to copy and paste the correct network interfaces.
Choose from the drop-down menu whether the appliance is equipped with at least version 2.3 of OpenVPN.
Choose from the drop-down menu which port should be used as modem port.
The management of the gateways can be done using the buttons at the bottom of the table:
This option allows a new gateway to be added to the list. Its configuration can be carried out by double-clicking on the fields of the new row.
By clicking on this button, the highlighted gateway is eliminated from the list. This button is active only when one row is selected.
Warning
The deletion of a row is immediate and can not be reversed.
Click on this widget to show a list of Endian appliances and their default values to be used in the table above.
The logs of the Switchboard encompass all events that happen on all the various object (e.g., gateways, user groups etc.) that are managed by the Switchboard and can be reached only from the Switchboard menu, unlike all other logs which record the system events, accessible from Menubar ‣ Logs.
This page contains a table with the list of all events that took place on the switchboard. Above the table, the Export as CSV format button allows to download the log file in CSV format.
Each line of the table represents one event and contains the following information about it. Events concern either a connection to a remote device or some administrative tasks like user management or the addition or removal of an application.
Date: The time stamp of the event, i.e., the date and time when it happened.
Action: A keyword associated to the event. Each keyword designates a precise event and is almost self-explanatory. In alphabetical order, they are:
DEVICECREATE, DEVICEDELETE, DEVICEEDIT, GATEWAYCREATE, GATEWAYEDIT, GROUPCREATE, SYSTEMBOOT, TUNNELACTIVE, TUNNELINACTIVE, USERCREATE, USERDELETE, USEREDIT, USERLOGOFF, USERLOGON.
Note
TUNNELACTIVE and TUNNELINACTIVE refer to the creation of an OpenVPN tunnel from a client workstation to an endpoint.
User: The user who carried out the action.
Target user: The user that was the object of the action.
Gateway: In case of a connection to a device, the gateway used.
Endpoint: The endpoint to which a connection has been established or terminated.
Application: The application that has been modified.
Profile: The application profile that has been modified.
New in version 5.0.5.
The Endian Management Center is a module implemented with the main purpose to simplify the administration of all Endian gateways connected to the Switchboard. Additional features are the ability to keep the configuration of all gateways synchronised, to define different profiles to configure the gateways, and to store and show the history of configuration changes for the gateways in each profile. More details below.
The Management Center Explained
The Endian Management Center module allows the remote management of all the gateways registered with the Switchboard, to maintain a repository of their configuration, and to keep all their configuration synchronised with a reference gateway called Gold Gateway. While from the users’ perspective this module is easy to use, under the hood there are several points to highlight in order to understand how the module operates and interacts with the remote gateways. In the reminder, the most important features of the Endian Management Center are presented.
Communication between the Endian Management Center and the remote gateways uses the Jabber (XMPP) protocol. This is the most important difference between how the Switchboard, which uses OpenVPN, and the Endian Management Center interact with the remote devices they manage. This implies that the same device can be marked as online on the Switchboard but offline on the Endian Management Center or vice versa.
For this reason, the following ports are opened on the Endian UTM Appliance (and can be seen under Firewall ‣ System Access ‣ Show rules of system services) to allow a seamless connection between the Management Center and the gateways:
Portal TCP 443.
Jabber TCP 5222.
OpenVPN TCP+UDP 1194.
Note
Port 1194 may depend upon the OpenVPN server configuration.
EMC profiles can be created on the Management Center to allow selective access and to the remote gateway’s modules. Many gateways can be associated with each profile, and one gateway within a profile will be elected as Gold Gateway, which is the one that acts as the model to which the other gateways will conform.
This special role introduces the next feature, the synchronisation of the gateways. As soon as the gold gateway is elected, its configuration is saved on the Endian Management Center and pushed to the other gateways associated to the profile. In the profile, it will be possible to choose among a number of modules whose configuration will be kept synchronised on all the other gateways within the profile.
But what is synchronised and how? The /var/efw/
configuration directory on the Gold Gateway is copied in a
repository on the Endian Management Center, complete with a revision history, and can
then be pushed to all the gateways in the profile. When a gateway
receives a configuration, it will be stored on the
/var/emc/ folder. In case of discrepancies between the
configuration in the two folders, the local /var/efw/ takes
precedence. Similarly, whenever the status of a service differs on
the Gold Gateway and on one or more of the other gateways, the
status on the gateway takes precedence. For example, suppose that
the outgoing firewall is enabled on the Gold Gateway, but it has
been disabled for some reasons (like, e.g., troubleshooting), on a
gateway, and the gateways are synchronised: the outgoing firewall
will remain disabled.
Whenever the configuration is pushed on the gateways, the gateway is also updated: the list of packages is retrieved and, if necessary, it is upgraded. Only after these two task have been completed successfully, the configuration is sent to the gateway.
Warning
Care must be taken when an upgrade is required after the installation of some packages, since there is currently no mechanism that inform of a necessary reboot on the remote gateways.
The page contains a table with the list of gateways that can be managed by the Endian Management Center, with the following data:
The Name which must be unique.
The Status, either online of offline.
The Profile, which defines what parts of the configuration will be pushed to the device.
The Actions that can be done on the device, which are:
To edit the gateway. See below for details.
To fetch the configuration. By clicking on this icon, the content
of the /var/efw/ directory on the gateway will be
retrieved and copied to the Switchboard.
To view the current configuration of the gateway and its changes over time. Since all the previous configurations are stored in a git repository, it is possible to highlight changes between versions.
To download the current configuration of the gateway.
Note
Some actions may not be available to some users, depending on their permissions.
Although the configuration of the gateways is saved on a Switchboard’s local repository, this function neither constitutes a backup, nor is intended as a replacement of a backup policy.
When clicking on the  icon, information about the current status
of the system are retrieved and shown in a new page, that is organised
in tabs that also present several configuration options.
icon, information about the current status
of the system are retrieved and shown in a new page, that is organised
in tabs that also present several configuration options.
In this tab, the following information are shown.
The name given to the gateway. It must be unique and can not be changed.
The organization to which the device belongs to.
An optional description of the gateway.
The profile associated with the device, chosen from the drop-down menu. Only one single profile can be associated to a device.
This tab reports information about the VPN connection:
Name: the name of the VPN connection.
Status: whether the gateway is connected to the VPN.
Actions: Currently the only available action is to enable or disable the VPN tunnel, by ticking the checkbox.
Note
A manual change of the status here will be reflected accordingly in the Switchboard dashboard.
This tab show the list of all the packages installed on the gateway, including their version. The gateway must be online or have already been connected once to show the list of packages.
The appearance of this page is very similar to the one in the updates page (System ‣ Updates). A message is displayed and, if the gateway is updated, shows the date of the last ungrade and last check for updates, otherwise it shows a list of packages that need to be updated. Two actions are available here:
A manual check for updated packages is started, and any upgradable package found is listed here.
The update process is launched: The system downloads and installs the new packages, replacing the old ones.
In this tab a list of the processes running on the gateway is shown, with a number of information, similarly to the output of the top command. For each process, these are the information shown:
PID. The unique Process ID
Name. The name of the running process.
CPU. The CPU time used by the process since its start.
Priority. The priority of the process, which is usually a positive number lower than 20. The string RT means the process runs with real time priority.
Virtual memory. The amount of virtual memory used, in Kilobytes.
User. The user who launched the process.
This tabs shows a list of the jobs and their status on the gateway. A job is a process on an Endian device that is managed by the jobseninge. The information shown are:
Name. The job name.
Status. A string displaying the status of the job. See below for details.
This tab encompasses a lot of information about the gateway, grouped in five panels. They are the same that can be seen on Endian Network.
General Info. Hardware, kernel version, load average, uptime and few other data at a glance.
Network. The routing table of the gateway.
Disks. The partitions defined on the gateway and the space available on them,
Memory. The RAM usage,
Hardware. The various hardware pieces of the gateway like network interfaces, USB Plugs, VGA adapters and so on.
Hint
These information reflect those present in Endian Network, under an appliance’s Hardware tab.
Jobsengine’s status messages.
Jobsengine status messages are composed by three parts and some typical examples include: start.ok/waiting, stop.err/waiting, or start.ok/restart pending.
The first part (before the dot) is either start or stop and shows whether the job is running or not.
The middle part (between the dot and the slash) is either ok or err and show whether the last invocation of the job was successful or not.
The third and last part (after the slash) is usually waiting, but if some additional process, required by the job, is starting, or if the job is restarting, this part can be restart pending.
This page allows to define EMC’s Profiles, which are not to be confused with the Switchboard’s Application Profiles. An EMC Profile consists of a list of modules of an Endian appliance. The configuration of those modules is stored on the Switchboard and will be pushed to new gateways as soon as they are registered to the Switchboard. This ability allows to keep synchronised the configuration of all devices of the same type.
The page shows the profiles that have already been defined, with the following information:
The unique Name, which includes also the organization it belongs to.
A description of the profile.
The available Actions:
 To edit the profile.
To edit the profile.
 To remove the profile.
To remove the profile.
To create a new profile, click on the Add Profile link above the table. The page that opens contains two tabs, Profile and Devices, each containing configuration options.
In this tab, the following options are available:
The unique name given to the profile.
Hint
It must consist of alphanumeric characters (0-9, a-z, A-Z), underscores (_), dash (-), dots (.), or ats (@). Spaces and other special characters are not accepted.
The organization for which the profile will be available. by default, a profile will be available to all organizations.
A description of the profile.
Select which modules are part of the profile and that should be pushed to the gateway.
This page appears as soon as at least one gateway has been associated to the profile, and is the most important one: Indeed, it is not just a configuration page, but it also allows to manage which profile is associated to a gateway and to carry out bulk actions on all gateways. The page is divided into three panels: Gold gateway, Bulk actions, and Devices.
In this panel the gold gateway can be configured and managed. The following options and actions are available.
Select which of the devices managed from the Endian Management Center should act as the gold gateway. By clicking on the Change button it would be possible to modify the choice.
The product of the gold gateway.
The software version installed on the gold gateway
Note
The product and version are automatically fetched when the gold gateway is selected and match those shown on Endian Network.
Create a copy of the current /var/efw/ directory and copy
in the local repository.
Opens a new page that shows the repository with all the versions of the configuration.
Bulk actions are executed on all gateways in order to synchronise their status with the gold gateway and are the following. When clicking on a bulk action, a pop up will appear and ask for confirmation.
Update the list of packages.
Install the new packages.
Warning
No automatic reboot is executed after installing packages, even if necessary, so make sure that gateways are rebooted as soon as possible after the installation of the packages.
Copy the current configuration of the gold gateway to the other.
Note
Before the configuration is pushed to the gateways, these are also updated. This implies that also the previous two actions (update and upgrade packages) are pushed to the gateways.
When a bulk action is launched, these three buttons remain disabled. Only when the action terminates (either successfully or not, see next section), another action can be executed.
This page shows information about each gateway managed by the Endian Management Center and its status.
The unique name of the gateway and its status, which is either online or offline.
The gateway’s model.
The number of available updates
The status of the gateway, compared with the gold gateway. which is marked with the special GOLD GATEWAY label. The provisioning can be either OK or NOT SYNC.
When a bulk action has been launched, this column shows the progress. The DONE label means that the action has been successful, while the TIMEOUT label means that the action was not successful. Other label are displayed that show the current action executed on the gateway.
From here it is possible to download the 4i Connect Client, that can be installed on a local workstation and used for both the management of the Switchboard and for launching a direct connection to the remote devices, using the application profiles defined on the Switchboard and provided that the necessary applications are installed on the workstation.
The documentation for the Switchboard API is available online.
Version 3.2
Version 3.0
Version 2.5
Version 2.4
Version 2.3
Version 2.2
Version 2.1