Virtual Private Networks or VPNs allow two networks to connect directly to each other over another network such as the Internet. All data is transmitted securely over an encrypted tunnel, hidden from prying eyes. Similarly, a single computer can also connect to another network using the same facilities. In Endian Firewall both OpenVPN and IPSec protocols are used to create VPNs.
Endian Firewall can easily establish VPNs to other Endian Firewalls. EFW can also inter-operate with just about any VPN product that supports OpenVPN, IPSec and standard encryption technologies such as 3DES. VPN connections in Endian Firewall are defined as Net-to-Net or Host-to-Net. This is 100% optional, so you may safely ignore this section if you do not wish to make use of this feature.
Most modern operating systems have support for IPSec. This includes Windows, Macintosh OSX, Linux and most Unix variants. Unfortunately, the tools needed to provide this support vary greatly and may be difficult to set up. OpenVPN setup is way easier than IPSec. It runs on Linux, Windows 2000/XP and higher, OpenBSD, FreeBSD, NetBSD, Mac OS X, and Solaris.
In the commercial version of Endian Firewall a user friendly OpenVPN client for Windows, Linux and MacOSX is available.
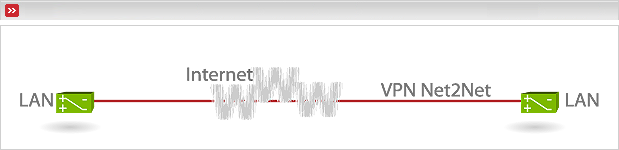
Net-to-net (or gateway-to-gateway) VPNs link two or more private networks across the Internet by creating a crypted “tunnel”. In a net-to-net VPN, at least one of the networks involved must be connected to the Internet with an Endian Firewall. The other network(s) can be connected to an Endian Firewall or another IPSec or OpenVPN enabled router or firewall. These router/firewalls have public IP addresses assigned by an ISP and are most likely using Network Address Translation (NAT), hence the term Net-to-Net.
If desired, a VPN can be created between wireless machines on your BLUE network and Endian Firewall. This ensures that traffic on your BLUE network cannot be intercepted with wireless sniffers.
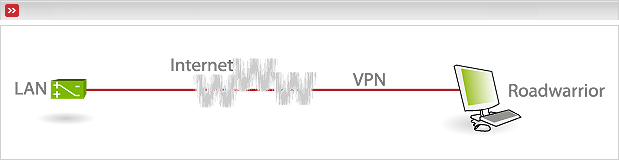
We are speaking of a Host-to-Net connection when Endian Firewall is on one end of the VPN tunnel and a remote or mobile user is on the other end. The mobile user is most likely to be a laptop user with a dynamic public IP address assigned by an ISP, hence the terms Host-to-Net or Roadwarrior.