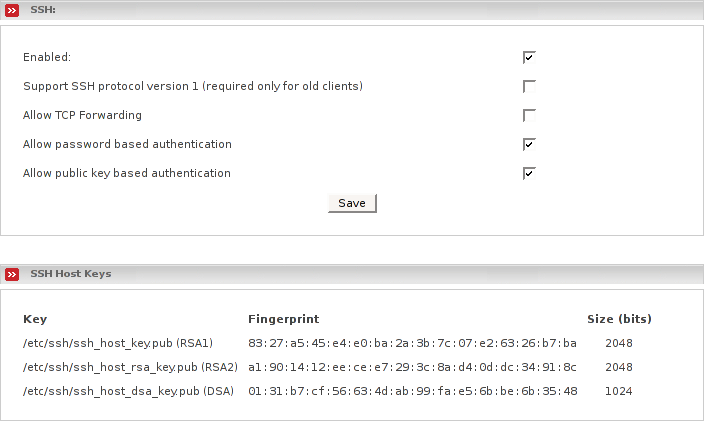
The SSH subsection of this AW allows you to decide if remote SSH access is available on your Endian Firewall or not. By placing a checkmark in the box you will activate remote SSH access. It is also possible to configure several SSH daemon parameters from this web page. The SSH option is disabled by default and we would advise enabling it only as needed and then disabling it afterwards.
Note
The SSH port on the EFW machine is the standard 22 (not switched to 222 like in IpCop).
The following SSH options are available from the web page:
- Enabled:
Checking this box enables SSH. Unless you use external access, SSH will only be available from the GREEN network. With SSH enabled it is possible for anyone with the Endian Firewall root password to log into your firewall at the command prompt.
- Support SSH protocol version 1 (required only for old clients)
Checking this box enables support of SSH version 1 clients. Use of this option is strongly discouraged. There are known vulnerabilities with SSH version 1. Use this option only for temporary access, if you only have SSH version 1 clients and there is no way to upgrade to SSH version 2. Most, if not all, of the current SSH clients support version 2. Upgrade your clients if at all possible.
- Allow TCP Forwarding
Checking this box, allows you to create SSH encrypted tunnels between machines inside your firewall and external users.
What use is this when EFW already has a VPN?
You are on the road and something goes wrong with one of your servers. You haven't set up a road warrior VPN connection. If you know your EFW root password you can use SSH port forwarding to get through your firewall and get access to a server on one of your protected networks. These next few paragraphs will discuss how to do this, assuming you have a Telnet server running on an internal computer at 10.0.0.20. It also assumes your remote machine is a Linux machine. The putty SSH command on Windows has the same capabilities, but they are accessed via dialog boxes. You may already have done one or more of the first two steps.
Enable or have someone else enable external access for port 10443, the HTTPS port.
Use the EFW web pages to enable SSH access, port forwarding and external access for port 22.
Create an SSH tunnel between your remote machine and the internal server running an SSH daemon by issuing the command:
$ ssh -N -f -L 12345:10.0.0.20:23 root@efw- -N
in conjunction with -f, tells SSH to run in the background without terminating. If you use this option, you will have to remember to use kill to terminate the SSH process. As an alternative, you may want to add the command sleep 100 to the end of the command line, and not use the -N option. If you do this the SSH invoked by the ssh command will terminate after 100 seconds, but the telnet session and its tunnel will not terminate.
- -f
option to run SSH in the background.
- -L
tells SSH to build a port forwarding tunnel as specified by the next parameters.
- 12345
The local port that will be used to tunnel to the remote service. This should be greater than 1024, otherwise you must be running as root to bind to well known ports.
- 10.0.0.20
This is the GREEN address of the remote server.
- 23
This specifies the remote port number to be used, Telnet.
- root@efw
Finally, this specifies you will be using your Endian Firewall as the port forwarding agent. You need a user ID to log in as, and the only one available is root. You will be prompted for EFW's root password.
Finally, log into the remote Telnet using the tunnel.
$ telnet localhost 12345localhost is the machine you are running on. The loopback address 127.0.0.1 is defined as localhost. 12345 is the local tunnel port specified on the previous command.
There is a tutorial on SSH port forwarding at Dev Shed.
- Allow password based authentication
Allows users to log into the Endian Firewall using the root password. If you decide to turn this off, set up your SSH key files, first and then verify you can log in using your key files.
- Allow public key based authentication
By checking this box, public key authentication can be used by SSH. This is the preferred method of securing EFW using SSH. This article has a discussion about using SSH-keygen to generate RSA keys and how to use them with SSH.
This section lists the host key fingerprints used by SSH on EFW to verify you are opening a session with the right machine. The first time a session is opened, one of the fingerprints will be displayed by SSH and you will be asked to verify it's correct. If you wish, you can verify it by looking at this web page.