The Network Status subsection displays the following in top-down order:
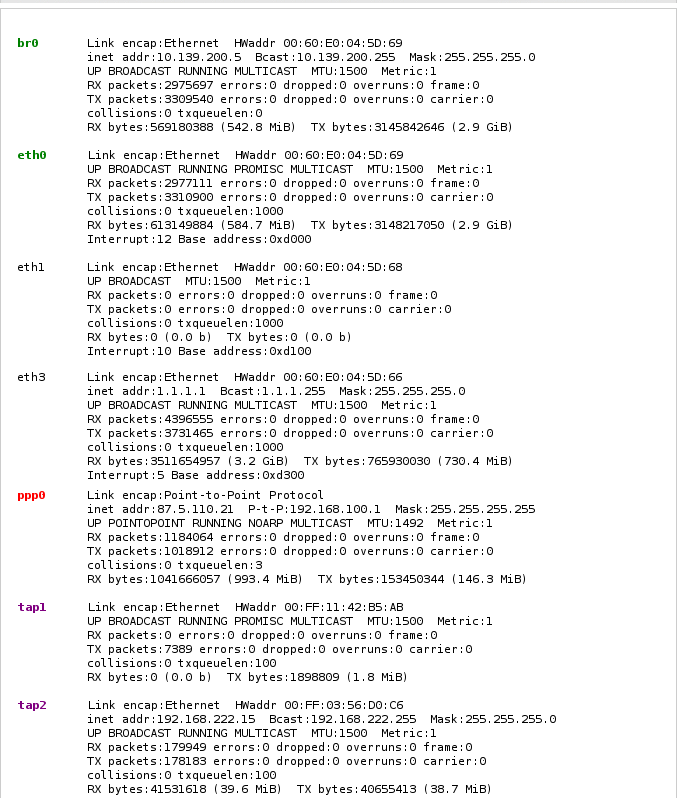
Interfaces - This section displays information about all your network devices. This includes PPP, OpenVPN, IPSec, Loopback, etc. Basically this is the output of ifconfig
You will find each interface name colored with the appropriate zones color. The purple color identifies interfaces which belongs to a VPN. Since each zone in reality is a bridge to which all assigned interfaces are joined, you need to take a look at the interfaces beginning with br. They are the real zone interfaces which are holding the IP addresses you configured, however they are virtual interfaces. The interfaces beginning with eth are the physically existing network cards. The interface called lo is the loopback interface. This one is needed to allow communication with the machine itself without leaving any real network card. You may also find interfaces beginning with tap. That interfaces will be used for openvpn tunnels.
Each interface shows a bunch of information at the right side. If you want to know more then it would probably be better to read the Network Administrators Guide. Here you will find a short description about the most important values:
- Link encap
Specifies the link type. Values like Ethernet, Local Loopback, Point-to-Point Protocol may appear here.
- HWaddr
The hardware address (MAC) of the respective interface
- inet addr
The IP address which has been assigned to the interface. You may notice that the interfaces which are part of a bridge do not have an IP address.
- Bcast
The broadcast address which has been assigned to the interface.
- Mask
The network mask which has been assigned to the interface.
- RX/TX packets
This lines shows how many packets have been received or transmitted errorfree, how many errors occurred, how many packets were dropped - probably because of low memory - and how many were lost because of an overrun. Receiver overruns usually happen when packets come in faster than the kernel can service the last interrupt.
- RX/TX bytes
This lines show the data volume which has been received or transmitted by this interface.
Between the lines descibed above you find a line with information about the status and options set for the respective interface. You probably may be concerned about the PROMISC option which is set for most of the interfaces. Most physically mounted network cards are put into promiscuous mode since they are all part of a bridge and therefore need to be in this mode.
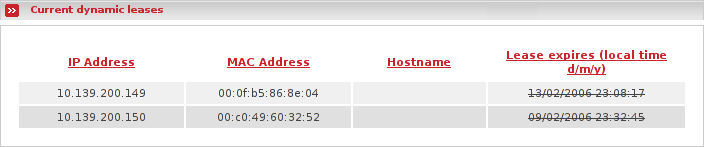
Displays the DHCP configuration on your RED interfaces if the DHCP is required by your internet connection.
Displays the contents of the /var/state/dhcp/dhcpd.leases file if the DHCP server is enabled. The current dynamic leases are listed, with hostnames if available, and expiry dates.
Leases that have expired are stroke through.
Note
This section will only be visible if DHCP is enabled. Refer to the section on the DHCP Server for details.
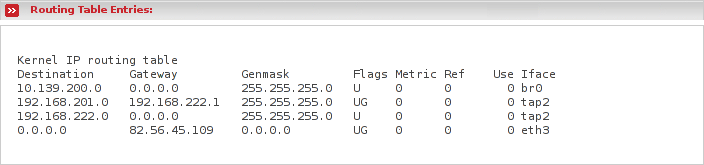
This is the output of route -n, which shows the kernel routing table. The routing table lets the kernel know which block of IP addresses it can find behind which interface. Most of the lines which you see in the output contain information about your local networks. But since you need the firewall to have connections to the internet, which in fact are all destinations with IP addresses which are not directly known to the kernel, an entry which sends all packets to a specific IP address in hope that that host knows more about the delivery, is needed. That specific host is called default gateway. Within your output you may identify this configuration in the line with destination network address 0.0.0.0, which means all destinations.
Besides, each line shows you the following information:
- Destination
Specifies the destination network address. The kernel compares the destination ip address of each packet passing through it with this destination network address and so searches an entry to which network the ip address may belong to.
- Gateway
Specifies the gateway, which is the host to which the packet should be sent. 0.0.0.0 means, put it on the media (LAN) and do not send it to a specific host.
- Genmask
The network mask of the respective network.
- Flags
The only interesting flags would be the following:
U - means that the route is up.
G - means that the route uses the gateway address specified by gateway.
H - means that the route entry is a host route, which is true only for a host instead of a whole network. You may notice that the netmask in this case is 255.255.255.255.
- Iface
Specifies the interface through which the kernel will send the packets if the respective routing entry applies.
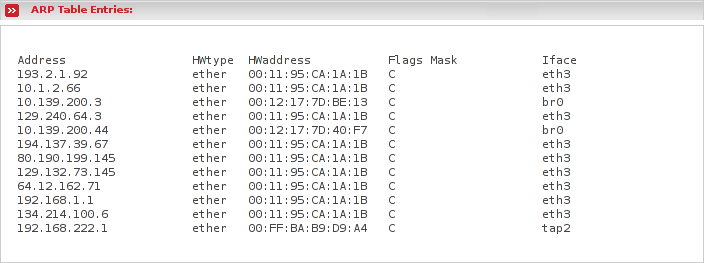
This is the output of arp -n, which displays the ARP cache. In LANs on the deepest layer the network interfaces will not be addressed by an IP addres, but by the MAC address instead. In order to let the kernel know which IP address is assigned to which MAC address, the kernel sends an ARP request which basically is a broadcast packet which asks all connected network interfaces if they have the desired IP address. The one who has the relevant IP address, responds with an ARP response including its MAC address. In order for the kernel not to send ARP requests all the time, responses will be cached in the ARP table for a while.
The output will show you the actual cached assignements of the ip address (Address) to MAC address (HWaddress). Additionally you see also behind which interface you can find the network card with the respective MAC address (Iface).
You may notice lines with [incomplete] instead of a MAC address. This will happen if someone tried to reach an IP address which is currently not available because it is wrong or the device with the assigned IP address is currently down or not connected.