In this section you can configure some useful options.
The page is divided in four sections. Each of them are described below:
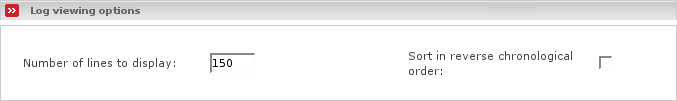
- Log viewing options
Lets you take effect on the output of the log lines:
- Number of lines to display
Specifies how many log lines you want the log viewer to display on one page.
- Sort in reverse chronological order
Tick this on if you'd like the log viewer to display chronologically newer log lines first.
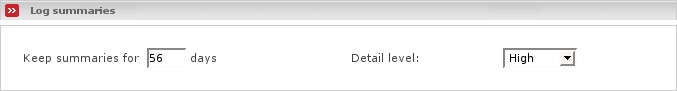
- Log summaries
This lets you configure the summary page, which will be described later in this document:
- Log summaries for xxx days
Lets you define for how many days you would like to save the daily summaries on disk.
- Detail level
Lets you decide the detail level of the log summary. You can choose from the following possibilities: Low, Medium, High. Due to this configuration the summary will provide you with less, more or much information.
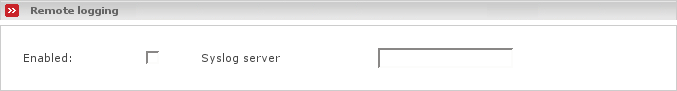
- Remote logging
It is possible to let Endian firewall log all its log files also to a remote syslog server. This is very useful if you would like to have all the logs of your company on one centralized log server and it is useful for example to have access to log files in case of a fatal disaster. In order to enable remote logging you need to provide the hostname or ip address of the remote syslog server in the text field labeled Syslog server and then tick on the checkbox Enabled. Endian Firewall then will log as well to the remote syslog server as to local log files.
Note
Currently not every service is able to use syslog. Therefore some can only write down to log files and cannot log to a remote syslog server. Services which currently cannot use syslog are: all sort of HTTP services (administration web server, HTTP proxy, HTTP content filter, HAVP), FTP proxy, IDS (snort).
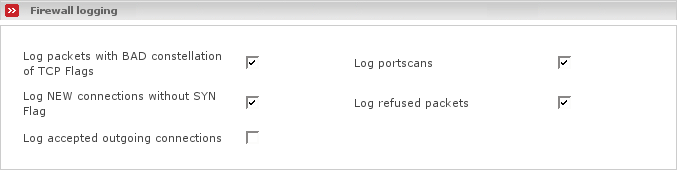
- Firewall logging
Usually if Endian Firewall has a public ip address and therefore is the door to the outside, there are very much packets that will be blocked by the firewall. Not all of these are hostile attempts of attackers, but will nevertheless be logged and create much data. Here you have the possibility to globally configure what you would like to have logged and what not:
- Log packets with BAD constellation of TCP flags
TCP allows everybody to set flags in constellations which make no sense at all. Such constellations may confuse firewalls and/or computers in general and allow an attacker to gather more information than you would like to share. Especially portscanners do this. Endian Firewall blocks such attempts. Tick this on if you want to have it logged. You will find such attempts in the firewall log resulting as packets which passed the chain BADTCP.
- Log portscans
You may enable portscan detection by ticking this checkbox on. The portscan detection will be performed using the netfilter psd match. You will find the logged portscans in the firewall log resulting as packets which passed the chain PORTSCAN.
Note
Portscans will never be blocked! They will only be logged! If you have not configured any ports to be forwarded a portscan of an Endian Firewall will not reveal anything of interest to the attacker since there is nothing open.
- Log NEW connections without SYN flag
Packets which should establish a TCP connection must have set the SYN flag. If it is not set, it is not sane. Endian Firewall will block such packets and you can log the attempts if you tick this checkbox on.
- Log refused packets
If you tick this on, Endian Firewall will log all connection attempts which have been denied by Endian Firewall. Since Endian Firewall as default denies all connection attempts and allows only what you have defined, this certainly will lead to a bunch of unneeded data, so you may toggle this off. It may be useful to check which ports you need to open for applications that are using ports you don't know.
- Log accepted outgoing connections
Tick this on if you would like to globally log all connections which have successfully passed Endian Firewall without being dropped. You can use this to test if your newly created rules are correct as this allows you to see the connections made by your applications.
Note
Check your local law! Enabling this may be prohibited by privacy law in most countries! But some countries may enforce you by law to enable this (For example the antiterror law in Italy). If you need to enable it, think about to backup your logs since you probably also need them after a case of fatal disaster! Ensure that nobody has access to backups and log files (privacy law)!