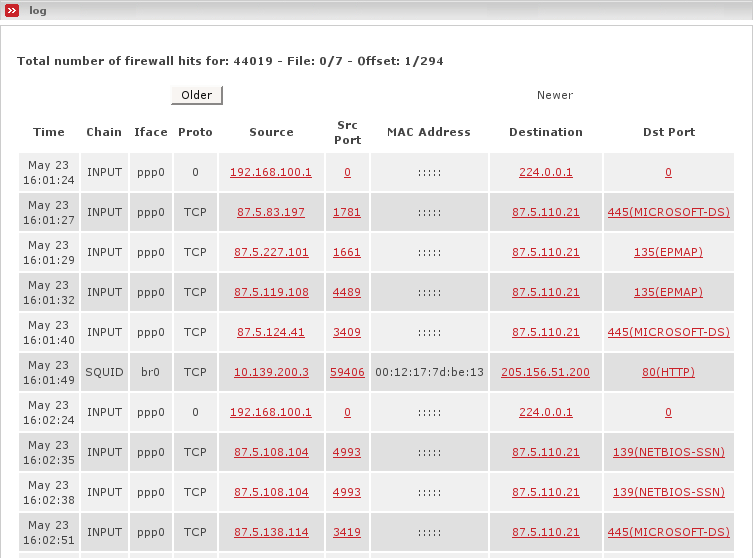
This page shows data packets that have been logged by the EFW firewall.
Note
Not all denied packets are hostile attempts by crackers to gain access to your machine. Blocked packets commonly occur for a number of harmless reasons and many can be safely ignored. Among these may be attempted connections to the "ident/auth" port (113), which are blocked by default in Endian Firewall.
The controls on this page are the basic elements that are described in detail in the introduction.
The Log: section of this page contains an entry for each of the packets that were dropped by the firewall. Included is:
the time of the event
the firewall Chain which was responsible for the log entry
the interface (iface) through which the packet came in
the protocol (Proto) used for that packet.
the source ip address
the source port (src port)
the MAC address of the sender
Note
This will be blank if the respective interface does not support MAC. For example all types of PPP connections.
the Destination ip address
the destination port (dst port) to which the client connected.
You can obtain information about the listed IP addresses by clicking on an IP Address. Endian Firewall performs a DNS lookup and reports any available information about its registration, ownership and geographical position. By clicking on a port number you will get some information about the service which normally uses this port.