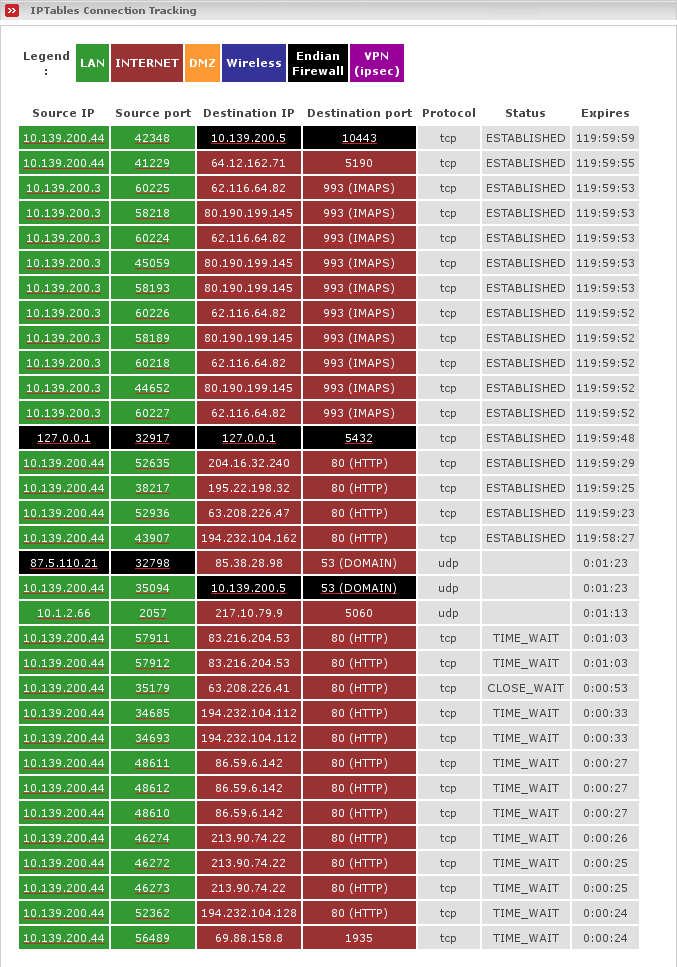
Endian Firewall uses the Linux Netfilter or IPTables firewall facility to maintain a stateful firewall. Stateful firewalls keep track of connections to and from all GREEN, BLUE and ORANGE network IP addresses, based on both the source and destination IP addresses and ports, as well as the state of the connection itself. After a connection is established involving protected machines, only packets consistent with the current state of the connection are allowed their way through the Endian Firewall.
The IPTables Connection Tracking window shows the IPTables connections. Connection end points are color-coded based on their network location. The color-coding legend is displayed at the top of the page. Information on individual connections is displayed next. Each connection from or to your networks is shown.
Note
Click on an IP Address to do a reverse DNS lookup.
You may notice that connections which will be intercepted by a transparent proxy will be nevertheless shown here instead of both a connection from client to the firewall and from the firewall to the remote host, as one may assume. In fact you will see all of them. The connection from your client to the proxy, the connection from the proxy to the remote host and furthermore the intercepted connection from your client to the remote host, since that is the real connection which has been established.The other two connections are only consequences of the redirect to the proxy which of course will be made by the kernel.